In this new blog, exclusively contributing to RCR Wireless, Siân Morgan, Research Director for Wireless LAN market, will explore whether these are the reasons that Wi-Fi 6E adoption has lagged, or whether other factors could be preventing access to the 1200 MHz of spectrum that was supposed to bring us better-performing Wi-Fi.
After being canceled in 2021 and postponed numerous months this year, the 2022 edition of the RSA Conference (RSAC) finally went into the books last week. Perhaps throwing a bit of caution to the wind–we are still in a pandemic after all–I met with nearly 40 vendors, 23 of them consisting of at least a 30-minute conversation and sometimes a couple of hours. In this blog, I summarize three takeaways from my week at RSAC 2022.
-
Buzzwords starting with ‘S’ keep coming: SWG, SD-WAN, SASE, and now SSE
The industry likes buzzwords that start with ‘S’ for whatever reason. The first ‘S’ came some twenty years ago with the arrival of SWG (Secure Web Gateway). Then came the second, SD-WAN, around a dozen years ago. After that, things were quiet until three years ago, when the third, SASE (Secure Access Service Edge), arrived. And the most recent, SSE (Security Service Edge), emerged last year and was in full view at RSAC 2022.
So why SSE? I blame the pandemic.
The pandemic caused an explosion in remote work that exposed severe inadequacies in enterprise IT networks to handle large numbers of remote workers. Fortunately, a crop of vendors–most with a SWG pedigree–were poised to help with their cloud-based security that was ideal for remote work. But SWG was a twenty-year-old marketing term and no longer cool. So instead, vendors wrapped themselves in the SASE mantel.
Confusion ensued since there were competing narratives by networking vendors, who ironically were primarily SD-WAN vendors and tended to remain more faithful to the original SASE premise of network and security convergence. So instead of picking sides, the industry created a new term, SSE, to let security vendors distinguish themselves. So yes, today’s emerging SSE vendors are, in many instances, yesterday’s SWG vendors. What’s different about SSE than prior SaaS-based SWGs is that now multiple security functions run in the cloud, such as CASB (Cloud Access Security Broker), ZTNA (Zero Trust Network Architecture), and FWaaS (Firewall-as-a-Service).
At RSAC, there wasn’t much talk about SD-WAN, but there was about SASE and SSE. It was humorous to hear certain security vendors sometimes use SASE and SSE in the same sentence as if they were freely interchangeable. On the one hand, they were trying hard to check off all the buzzwords, but on the other, a clear symptom of immature markets.
- Traditional Network Vendors Double Down and Get More SASE
Two stalwarts of the enterprise networking landscape, Cisco and Juniper, introduced updates to their SASE portfolio.
Cisco has had all the pieces to deploy SASE for some time, but there was no substantive integration. At RSAC, they introduced a new strategy to build a tighter integration between the Cisco SD-WAN and SSE (Umbrella) houses through a new unified manager based on the Meraki cloud management platform. Moreover, Cisco intends to sell everything, whether the cloud service or the hardware, as a subscription.
Meanwhile, Juniper has improved its recently introduced cloud-based security platform, Secure Edge. At RSAC, they announced the addition of CASB and DLP (Data Loss Prevention) services to Secure Edge. Like Cisco’s management approach, they also have a unified manager, Security Director, spanning SRX firewall elements and the cloud-based Secure Edge.
Both Cisco and Juniper are taking an interesting approach to SASE. It’s not all in the cloud since the networking/SD-WAN piece is still effectively on-prem, but nor is it disaggregated bag of parts. They’ve provided me with a lot of food for thought that I plan to infuse into my upcoming SASE research.
- Cloud Workload Security Remains a Smorgasbord
Over the last half-year, I’ve been meeting with vendors large and small to understand what cloud workload security, i.e., securing apps/workloads moving to a cloud architecture, means to them. From the onset, things have been cloudy (no pun intended).
On the one hand, we can all agree that the enterprise shift to the cloud is a significant change in IT architecture. The challenges, nuances, and caveats that must be dealt with during the journey from a traditional on-prem legacy app enterprise to a cloud-based, cloud-native app enterprise are significant. It’s a problem-rich environment that has given rise to dozens, if not hundreds, of security vendors.
On the other hand, the marketing most cloud-focused vendors use to describe themselves is on the verge of hyperbole. But it makes some sense why this is. Considering there are so many problems and challenges to solve, there isn’t any one company that solves them all or even close. So in a landscape that still requires many technologies from many vendors to solve most cloud problems, what does an individual vendor need to stand out? That answer is that they lean heavily on marketing and make it seem like they cover more than they do.
At RSAC, I met with a handful of cloud-focused security vendors, which only reinforced my conviction that it is a smorgasbord of products and overly creative marketing and far from being a single product or even a handful of solutions. Some vendors focus on threat detection. Some focus on risk and compliance. Others focus on the identity implications. Others seek to protect container communication. It’s a literal zoo of vendors. However, in this zoo of vendors, there are some emerging delineations.
Give me any cloud-focused vendor, and I’m pretty sure they’ll fit into one of three significant buckets, code security (coding/build security), IaaS/PaaS platform security (ensuring the runtime platform is as secure as possible), and app/container security (runtime security). I’ll be delving deeper into cloud workload security in an upcoming advanced research report. Stay tuned.
While not a numbered takeaway, my parting thought is that after two years of working exclusively via video conference, I’ve concluded that it doesn’t replace face-to-face meetings. There’s a quality and richness that face-to-face brings that current video conference technology fails to replicate. As such, I look forward to upcoming opportunities to engage the security community in person and the next RSAC in April 2023.
We’ve just wrapped up the 4Q21 reporting period for Dell’Oro Group’s enterprise network equipment programs, which include campus switches, enterprise data center switches, SD-WAN & enterprise routers, network security, and Wireless LAN. Enterprises include businesses of all sizes as well as government, education, and research entities. The equipment tracked in these programs can be used for wired or wireless data communication in private and secure networks.
Sales Hit Record Level in 2021
Despite a macro-economic environment that continues to be defined by supply constraints, our reports showed a strong rebound in the overall Enterprise Network Equipment market in 2021, following some stagnation in the prior year. Sales jumped 12% year-over-year (Y/Y), propelling the market to a record- level in 2021.
The strong performance was broad-based across all technology segments. Enterprise Routers, Wireless LAN, and Network Security were all up double-digits. In the meantime, Campus and Enterprise Data Center Switches were up mid-to-high single digits. All technology segments hit record-revenue level in 2021.
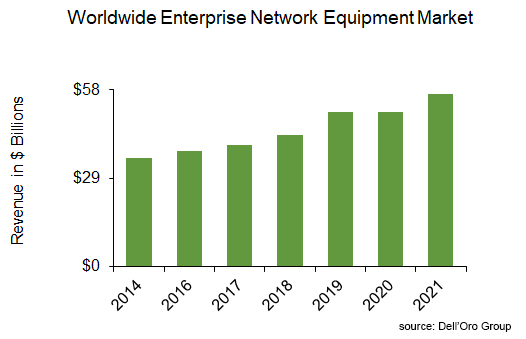

We have calculated that spending on enterprise network equipment rose by nearly $6.0 B in 2021. Security accounted for 40% of the increase in spending, while campus switches accounted for a quarter of the increase.
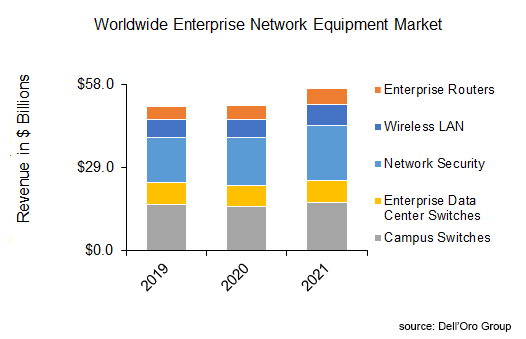

We attribute this broad-based recovery to the following:
- Continuing improvement in macro-economic conditions.
- Continuing government spending and stimulus around the world.
- Network upgrades in preparation for workers returning to the office full or part-time.
- Digital transformation initiatives, accelerated by the pandemic, are driving new network requirements and putting pressure on IT managers to upgrade their networks and add different security layers.
- Orders pulled in from future quarters, to mitigate ongoing supply challenges that are adversely affecting product availability, lead times, and prices.
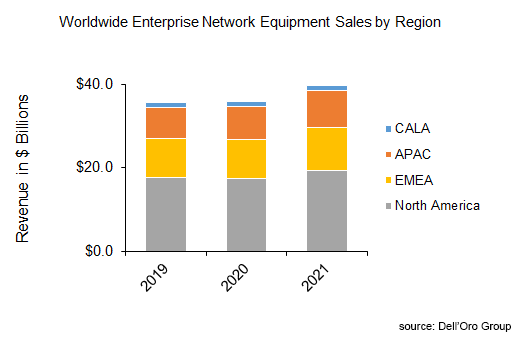
The 2021 robust performance in the Enterprise Network Equipment market was broad-based across all regions, except the Caribbean and Latin America, which was flattish (although showing a significant improvement from the high-single-digit decline registered last year).

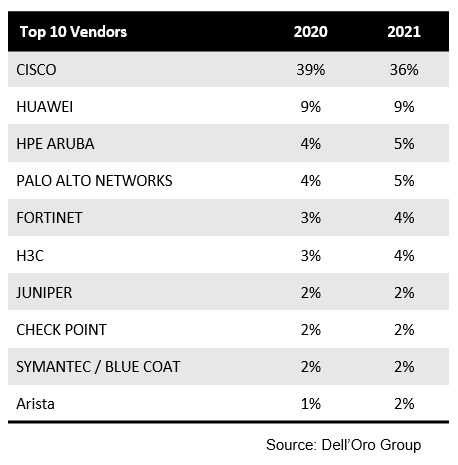
Cisco Loses Some Ground — Still Leads the Enterprise Network Equipment Market
The analysis shared in our reports showed no major change in vendors’ ranking. Cisco remains the only vendor with more than 10% share in the market, although the firm lost three points of revenue share in 2021. This share loss was broad-based across all technology segments, except WLAN. In the meantime, HPE Aruba, Palo Alto Networks, Fortinet, H3C, and Arista, gained one point of revenue share, each.
Nevertheless, we would like to note that the vendor landscape continues to be defined by a challenging supply environment and that some of the share shifts witnessed in 2021 may not be necessarily reflective of competitive displacement, but rather the timing of order fulfillment.

Robust Market Outlook for 2022
Despite a challenging supply environment that is expected to persist through most of 2022, Dell’Oro analysts are projecting strong double-digit revenue growth in the Enterprise Network Equipment market in 2022. This optimism is underpinned by healthy outlooks provided by most vendors as a result of increased visibility and robust backlogs. Additionally, ongoing supply challenges will continue to encourage customers to place advance orders, which will have a positive effect on bookings first, then a few months later, on revenues, depending on lead times.
Dell’Oro Group Enterprise Network Equipment research programs consist of the following: Campus switches, Enterprise Data Center Switches, SD-WAN & Enterprise Routers, Network Security, and Wireless LAN.
Scoring 2021 Predictions and Looking to 2022
Happy New Year! It’s an excellent opportunity to reflect on our 2021 predictions and share what we believe 2022 has in store. First, though, we need to temper our enthusiasm for projection by the fact the Covid pandemic continues to throw unexpected curveballs. Let us hope that the latest omicron variant is one of the last, if not the last. Nonetheless, let’s take stock and grade our predictions from a year ago first.
A year ago, we made three predictions for 2021:
- Enterprises will embrace the Work Anywhere securely mentality and make cloud-native SASE solutions mainstream
- Cloud-centric security will continue to grow faster than the overall market
- Firewall revenue will rebound after a meager 2020
On our first prediction, we can definitively say that enterprises embraced Work Anywhere based on the pandemic still forcing remote work in 2021. But beyond being forced remote workforce, we continued to hear how enterprises codified officially the role hybrid work will play long-term. Full-time remote work may not the new normal, but a blend between some days on-site and some remote will be. Hybrid work is no longer an employee perk but an expectation.
However, we did get wrong that SASE solutions would go mainstream in 2021. While SASE as a mandate did gain in importance, only a minority of enterprises deployed SASE fully. Moreover, a larger than expected swath of enterprises chose to stay with a traditional Firewall architecture.
Our second prediction of cloud-centric security revenue growing faster than the overall market has been spot on. We predicted revenue growth to be north of 20%, which has been for most of 2021 for the Software-as-a-Service (SaaS) and virtual appliance form factors that we categorize as cloud-centric security. While 4Q21 numbers are not in, we don’t expect any significant shift in their growth trajectory. As enterprises shift towards being entirely digital, multi-cloud, and mobile-friendly, they have been voting with their wallets and favoring SaaS and virtual solutions.
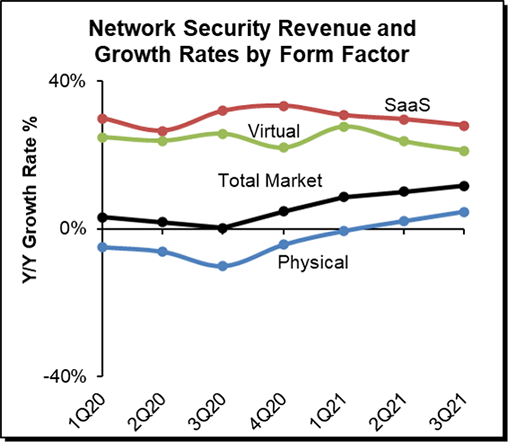

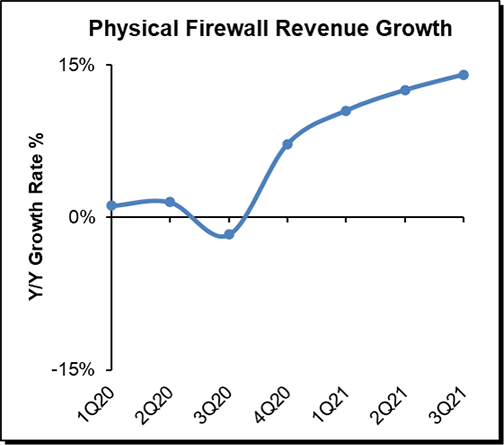
Our third prediction proved correct, with the physical firewall appliance market rebounding in 2021 from a tepid 2020. Enterprises that halted upgrades in 2020 are back in full swing doing refreshes to get greater capacity and the latest features.

Looking into 2022, we make the following three predictions:
1 – Only a minority of enterprises will fully deploy SASE in 2022, but all will force SASE of their vendors
If there’s any maxim in enterprise IT, change comes slowly for most enterprise IT teams. With SASE being a new architectural approach and causing a significant shift in networking and security operations, most enterprises are taking a methodical approach to SASE. Sure, there are a minority of enterprises capable and willing to give their entire WAN networking and security budget to a single pure-play SASE vendor to do full-blown SASE in one fell swoop. Still, the emerging reality is that in 2022 most enterprises will do things piece-meal by focusing on either the networking or security aspect of SASE first or using multiple vendors in their SASE deployment.
However, this doesn’t let vendors off the hook from SASE since most enterprises want their vendors to prove they know SASE and will help them in the journey. No enterprise wants to undertake either network or security transformation only to find out that their vendors can’t take them all the way.
Our 2022 SASE prediction is based on tracking the SASE market in two ways. The first is by what we call the SASE-related technology market, which is the total sum of all networking and security technologies that conceivably could be deployed in a SASE configuration. The second is by what we call the SASE technology market, which is the subset of the SASE-related market deployed in a SASE configuration. For full-year 2021, we expect the SASE-related technology market to nearly reach $4 B with year-over-year (Y/Y) growth topping 30%, while the SASE market may hit $500 M, representing highly robust growth of over 100% Y/Y.
2 – The physical Firewall market rebound will modulate, while cloud-centric security will continue to grow faster
Although we predicted a rebound in the physical Firewall market a year ago, its strength has surprised us. However, we expect the growth in the firewall market to level off. We believe the future of network security isn’t with the physical Firewall market, as it once was, but with those cloud-centric network security solutions that favor SaaS and virtual appliances as preferred embodiments.
3 – Firewall-as-a-Service will begin to cannibalize carrier-class Firewall physical appliances
In the last couple of years, Firewall-as-a-Service (FWaaS), or Cloud Firewalls, have started to pop up as an upsell feature of SaaS-based security solutions, notably in SaaS-based SWG and SASE solutions. The FWaaS in those solutions was primarily aimed at per-user or per-application type firewalling in remote user deployments. It wasn’t meant to replace the super-heavy iron of carrier-class physical firewalls that are still good hygiene in any large enterprise or carrier network. However, we have started to see both pre-IPO and public companies making motions and looking to use the power of the cloud to dethrone one of the last bastions where physical security appliances rule.
We predict that in 2022 at least several of the Fortune 100 will ditch their classic carrier-class Firewall hardware and go all-in on cloud-powered Firewalls.
A year from now, we’ll circle back and see what came true. We hope to repeat our good performance.

