Cisco intensified the secure branch battle today. During Cisco Live 2025, the company’s annual customer conference, it unveiled three new branch-focused elements: Secure Routers, Secure Firewalls, and the Mesh Policy Engine within Cisco Security Cloud Control. Rival vendors already consolidate routing and security in fewer product lines, so Cisco’s strategy warrants close review. This post explains what Cisco shipped, what competitive forces it faces, and why its three-product play emerged.
What Cisco Introduced at Cisco Live 2025
Cisco launched five Secure Router 8000-Series models—8100, 8200, 8300, 8400, 8500—positioned as successors to Catalyst 8000 Edge. Each appliance merges IOS XE routing, Catalyst SD-WAN, post-quantum MACsec, and an embedded Layer-7 firewall. From Cisco’s security business, the new Secure Firewall 200-Series arrived in parallel, running Firepower Threat Defense with Snort 3, encrypted traffic analytics, file sandboxing, and boasting up to 1.5 Gbps throughput.
Hardware innovation pairs with two software pillars. First, the Mesh Policy Engine unifies rule objects across routers, firewalls, and cloud enforcement points. Cisco positions it as part of the broader Hybrid Mesh Firewall framework. Second, Cisco Security Cloud Control became generally available in May 2025. The SaaS portal onboards devices, provides analytics, and houses the Mesh Policy Engine.
Cisco now addresses three branch personas. Secure Router serves WAN teams demanding rich routing and “good-enough” firewalling. Secure Firewall targets security teams that require full-featured firewalling (richer threat protection, encrypted traffic analytics). Meraki MX continues as a cloud-managed option for lean IT staff. The company argues that a shared SaaS policy plane offsets the complexity of sustaining three hardware families.
What Is Cisco Up Against?
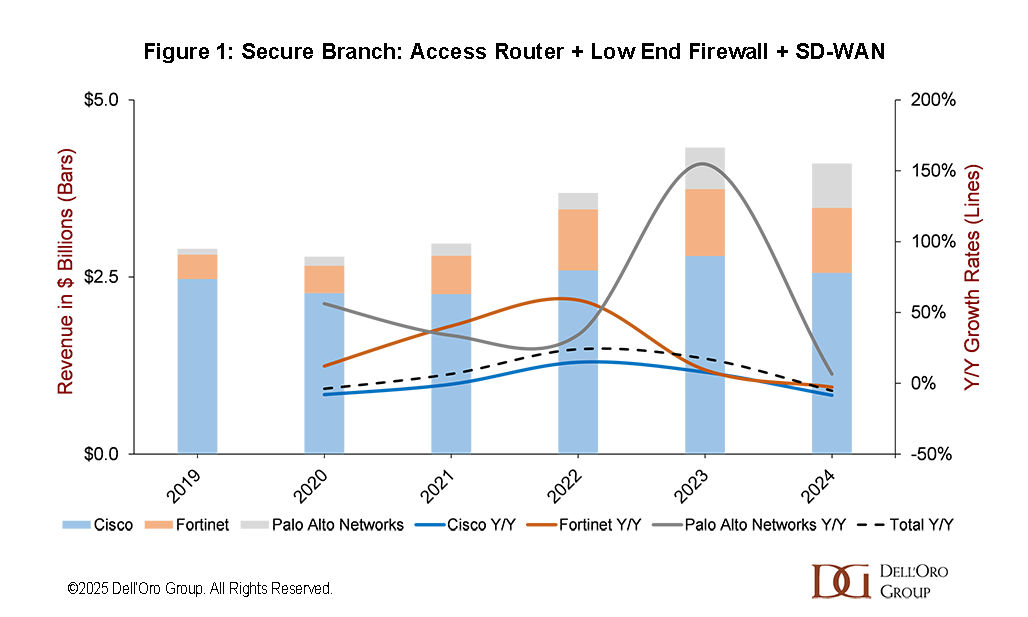
Figure 1 shows branch solution revenue—access routers, SD-WAN, and low-end firewalls—across Cisco, Fortinet, and Palo Alto Networks during 2019-2024. Cisco’s branch revenue edges from about $2.5 B in 2020 to $2.6 B in 2024, representing just a 1% five-year compounded annual growth rate (CAGR). Fortinet rises from $345 M to $919M, delivering 22% five-year CAGR. Palo Alto Networks expands from about $82 M to $625 M, a 50% five-year CAGR.
Fortinet competes with one hardware family—every FortiGate appliance ships with FortiOS, integrating NGFW, SD-WAN, ZTNA, and LAN control. Cloud or on-prem control planes push identical policy because the code base (FortiOS) is uniform across the portfolio.
Palo Alto Networks employs two product lines. PA-Series Strata firewalls run PAN-OS and focus on deep inspection. ION-Series devices, which trace their history to the acquisition of CloudGenix in 2020, integrate SD-WAN, PoE switching, optional 5G, and secure about 1 Gbps of traffic. Both device classes appear in Strata Cloud Manager, a single SaaS console introduced in late 2024. This platform also manages Prisma Access points of presence, offering one policy model across physical and cloud edges.
Why Cisco Launched What It Did?
The revenue chart illustrates Cisco’s challenge. Its branch growth has not kept pace with the security-first Fortinet and Palo Alto drive in the branch. Cisco’s installed base remains large, yet procurement teams now evaluate converged platforms that collapse routing, security, and LAN control. Fortinet delivers that promise through one appliance. Palo Alto offers a unified policy across two tightly linked lines. Cisco’s trio of Secure Router, Secure Firewall, and Meraki must deliver differentiated value or risk revenue erosion.
Strategic logic explains the three-product play. Cisco cannot abandon IOS XE routing, a core competency that WAN engineers value. Hence, the Secure Router retains familiar CLI, BGP, voice DSP roadmaps, and high routed throughput. The embedded firewall is streamlined to avoid burdening routing silicon, matching most branch risk profiles. The Secure Firewall family preserves Snort feature depth demanded by SOC teams. Firepower Threat Defense offers machine-learning heuristics, encrypted-visibility analytics, and file trajectory inspection that the router cannot yet match. Keeping Firepower intact minimizes migration friction for customers with existing Firepower or ASA estates. Meraki MX remains critical for small IT shops and managed service providers. Its Dashboard UI orchestrates Wi-Fi, switching, cameras, and security from one tab. Removing MX would alienate a rapidly growing segment that values zero-touch deployment.
The Mesh Policy Engine and Security Cloud Control are Cisco’s unification layer. They promise consistent rule intent across three operating systems—IOS XE, FTD, and Meraki OS—while allowing personas to keep their native workflows. The approach avoids a forced rip-and-replace but introduces integration risk. Success hinges on seamless policy translation, co-termed licensing, and synchronized feature releases.
Cisco also needed throughput parity. The new Secure Router family closes performance gaps without sacrificing routing or security functions. The Firewall 200-Series secures 1.5 Gbps, aligning with branch attack profiles where deep analytics outweigh raw speed.
Licensing complexity remains a concern. Cisco still sells DNA Advantage for SD-WAN, Threat Defense subscriptions for firewalls, and Meraki Enterprise licenses. The firm announced a Networking Subscription model for late 2025 that should co-term renewals. Whether this resolves budget headaches is an open question.
Cisco launched three discrete hardware lines because each maps to an entrenched persona, and because immediate unification would disrupt large customer bases. The Mesh Policy Engine aspires to hide complexity while preserving product heritage. Market data suggest the bet must succeed quickly to reclaim growth momentum.
Conclusion
Cisco refreshed its branch portfolio to confront accelerating competition. Secure Routers safeguard routing heritage, Secure Firewalls protect security parity, and Meraki maintains cloud simplicity. Fortinet and Palo Alto Networks leverage fewer product lines and show faster revenue expansion. The outcome now depends on Cisco’s ability to translate cross-platform policy seamlessly, simplify licensing, and deliver promised throughput gains.