…but a lot has changed since 2023
It has been a long slog, but on June 27th HPE finally received the go ahead to acquire Juniper, avoiding what could have been a protracted court battle in the US. By granting two limited concessions, HPE will now be able to absorb its smaller rival, in a bid to take on Cisco.
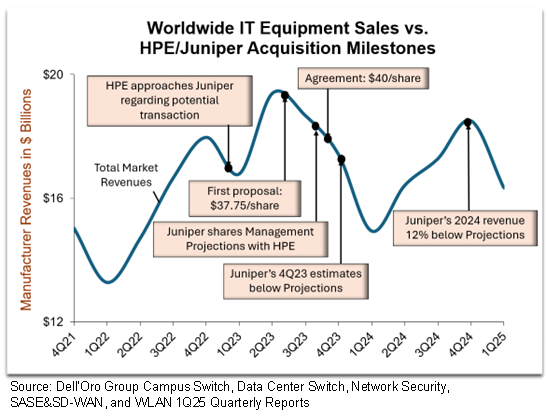
HPE’s intention to acquire Juniper for $40/share was announced a year and a half ago, but first CEO-level discussions related to a potential transaction occurred much before that, in February 2023. The engagement has been a long one, stretched out due to an executive change, price negotiations, regulatory hurdles, and the late intervention by the US Department of Justice. Meanwhile, a lot has changed in the IT equipment market.
Negotiations on a Roller Coaster
The last two years have been marked by pandemic shock waves and AI hype. When HPE’s CEO, Antonio Neri, first contacted Juniper about a potential transaction, the IT equipment market was showing signs of recovery after supply-challenged 2022. ChatGPT had launched just three months earlier, and the world was awestruck by its vast potential. Juniper’s early investments in an AI-driven architecture seemed prescient.
During the acquisition negotiations, the IT market skyrocketed, fueled by backlog fulfillment. However, by the end of 2023, the market was awash with excess inventory, and Juniper’s 4Q23 revenue expectations fell below the outlook executives shared with HPE in October. Fast forward a year, and Juniper’s 2024 revenues were 12% below the figure they had predicted during the negotiations.
Meanwhile, the AI landscape has also shifted.
The focused use of AI to automate network operations is becoming a mainstay for equipment vendors, narrowing Juniper’s lead in AIOps mindshare. Since Neri began negotiating with Juniper, CommScpope has introduced RUCKUS One, Extreme has begun taking beta customers on Platform ONE, and Cisco announced AI Canvas – all with AI-fueled features that compete with Juniper’s Mist.
Meanwhile, in a backdrop of economic uncertainty driven by global trade tensions, the broader use of AI may divert enterprise budgets over the next few years. To implement AI workloads in earnest, enterprises will need to spend on compute, AI models, applications and renewed cybersecurity, which could depress sales of networking equipment.
Where the Rubber Hits the Road
Now that the transaction is final, Juniper’s CEO Rami Rahim will take over HPE’s new networking division, consolidating Juniper’s business with HPE’s Intelligent Edge. Over half of Juniper’s sales are to enterprise customers, and this segment of the business will be fraught with drama.
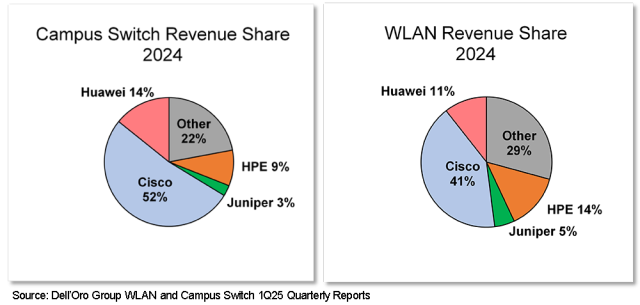
Until now, HPE’s Aruba products have competed head-to-head with Juniper Mist, and customers are concerned about the implications this acquisition will have on product roadmaps. The overlap is the highest in the WLAN and Campus Switch portfolios. While Juniper has the innovative microservices architecture, HPE has the higher market share, the closest competitor to networking behemoth Cisco.
Forces to Shape the Outcome
The concessions that HPE made in order to avoid a lawsuit from the U.S. Department of Justice are unlikely to present a large hurdle to the success of the acquisition. HPE is required to divest its Instant On business, which was designed for the SMB (Small Medium Business) segment and makes up a small percentage of HPE’s revenue. The combined HPE/Juniper entity is also required to auction two licenses to the WLAN Mist AIOps source code, while maintaining full ownership of the code for their own use. This may present an interesting opportunity for two American companies, but it is only a small piece of a successful enterprise IT strategy. The formula for competing with Cisco must involve a complete networking portfolio of hardware and software, along with a well-developed channel. A license to Mist source code can only go so far.
The real hurdles to this acquisition are deeper and more difficult to solve. Rami Rahim’s top priorities will include rationalizing road maps, obtaining the promised $450 Million in G&A (General and Administrative expense) savings, and incentivizing the sales teams and channel to toe the line. While navigating complex technological and organizational optimizations, HPE’s new networking division will have to face the following market forces:
-
Enterprises have “IT inertia”
In a worst-case combination, HPE could shut down the HPE or Juniper product lines with the smallest market share in each overlapping area. If every one of these customers got angry and changed to another vendor HPE-Juniper would lose about a quarter of its enterprise sales.
However, changing vendors is not something enterprises like to do. They have trained their staff, developed custom tools, and come to appreciate the features of their existing equipment. With the right positioning, HPE can embark on a slow product integration of Aruba Central and Mist, giving customers the best of both worlds and allowing a smooth transition.
-
Entrenchment of Goliath
Neri wants to challenge the market leader Cisco, but he will have to do more than incorporate Juniper’s enterprise revenues to become number one.
Networking vendors saw a glimmer of hope when, with the acquisition of Splunk, Cisco seemed set to leave its networking heritage behind to focus on AI, cloud and cyber security. However at Cisco Live in June, CEO Chuck Robbins appeared alongside Chief Product Officer Jeetu Patel with a message that the company may be pivoting to AI, but that networking was remaining at the core of Cisco’s strategy. (https://www.delloro.com/cisco-live-2025-networking-reappears-at-the-center-of-ciscos-ai-strategy/).
Cisco captures over a third of all enterprise market revenues. HPE and Juniper combined make up 8%. The plan to become number one will be a long-term project and will involve fighting IT inertia with a powerful product offering exuding simplicity and providing a lower-cost option to Cisco customers.
-
Security is another world
Security is a critical and rapidly growing priority for enterprises. With its acquisition of Juniper, HPE has entered the firewall market, creating opportunities to expand its sales and bolster its emerging SSE (Secure Service Edge) revenue.
However, the combined entity remains significantly behind established network security leaders like Palo Alto Networks and Fortinet, holding low single-digit market share in the SSE and firewall segments. It is worth noting that network security is one of the few segments that Cisco does not lead, and conversely, neither Palo Alto Networks nor Fortinet are among the leaders in other enterprise networking categories. HPE, as a traditional networking vendor, will face unique challenges in penetrating the network security market.
-
Culture is a Killer
The Harvard Business Review estimates that the majority of acquisitions fail to generate value due to hubris, social factors and a lack of understanding of the strengths that made the acquisition target a success. Both the Mist and Aruba brands have a strong recognition in IT circles, and bring different values to Juniper and HPE, leading to an acquisition with high potential for infighting, misunderstanding, and false assumptions.
It’s Theirs to Lose
Since acquiring Mist in 2018, Juniper has demonstrated the potential to take this cloud-managed, AI-driven architecture to the big leagues. While HPE Aruba’s premises-based enterprise portfolio has a dominant position, its cloud-managed solution has languished. Acquisition failure would represent a huge opportunity lost for Juniper and would cut HPE out of margin-rich recurring software streams that come with cloud-managed sales.
Meanwhile, established vendors such as Ubiquiti, Huawei, CommScope and Extreme are ready to take advantage of market confusion. In addition, startups with innovative technology and business structures are betting that enterprises frustrated with incumbents are keen to try something new. If HPE bungles this acquisition, there will be no shortage of competitors ready to pounce.
HPE’s established extensive channel and installed base, merged with Juniper’s Mist AIOps engine, could be the combination that gives Cisco a run for its money. Market digestion and a shift in AI spending may be mere bumps in the road. In the end, hubris, blind spots and brand culture could be the biggest risks of all.
- How the HPE-Juniper Acquisition Will Change the Enterprise Market, What the Numbers Say (Siân Morgan, Sameh Boujelbene, Mauricio Sanchez)
- HPE to acquire Juniper – WLAN market impacts (Siân Morgan)
- HPE Contributes better ‘Networking for AI’, Juniper Contributes better ‘AI for Networking’ (Sameh Boujelbene)
- HPE Acquires Juniper: What does this mean for its Network Security and SASE/SD-WAN aspirations? (Mauricio Sanchez)